Announcement posted by JC Indahaus Media 18 Dec 2013
As 2013 comes to an end, Unified Threat Management (UTM) has grown up.
What used to be an SMB security solution has now matured into a powerful platform for the midsize enterprise. The holy grail of defense-in-depth no longer requires costly point solutions, disparate management consoles, and hundreds of engineering hours to sift through log data. No, times have changed. Today, UTM is helping midsize enterprises overcome the complexity, performance and management challenges associated with protecting the corporate network.
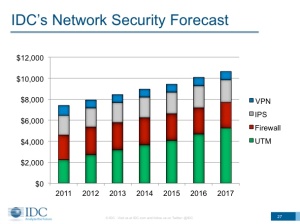
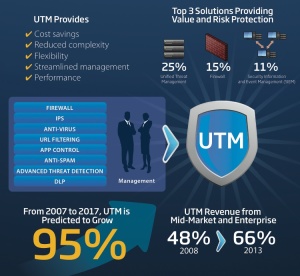
But, don’t take our word for it, the proof is in the data. According to IDC, from 2007 to 2017 UTM is predicted to grow 95 percent, and UTM revenue from mid-market and enterprise has grown 53 percent since 2008. Even more interesting, if you look below at the IDC graph from its most recent Network Security Forecast, it shows that UTM is the largest growing sub-function of the forecast (with the others having small or flat growth).
Below we’ll outline some of the challenges facing midsize enterprise, but you can also watch our recent IDC webinar with John Grady (research manager for security products and services) on this topic, or download our new IDC infographic, sponsored by WatchGuard Technologies, on UTM in the mid-market entitled “Protecting Your Midsize Enterprise with UTM.”
There are three key issues midsize organizations face today when it comes to network security:
1. Complexity
As the security perimeter has evolved, attack mechanisms have become increasingly sophisticated, and solutions to solve these problems have multiplied, security professionals are overwhelmed with the complexities of securing the network. Mobile devices, virtualization, and cloud applications – all of these create architectural concerns for midsize enterprises. And, since these organizations traditionally have less staff and budget, the realities of integrating complex point security solutions to address these problems becomes more unrealistic.
2. Performance
The Internet continues to grow (IDC and EMC estimate in the IDC Digital Universe Study, sponsored by EMC in December 2012, an increase from 2.8 to 40 zettabytes from 2010-2020), as does the shipments of mobile devices (19.8 percent by 2017). Organizations are using more applications, have unlimited sharing conduits, using rich media, and are connected all the time – online activity has exploded. Roll in cloud applications and all of a sudden you have tremendous traffic coming in and out of your network. The gateway appliance can’t be the bottleneck. It must deliver higher throughput, better connection rates, be scalable and offer layered security at the point of entry or exit (defense in depth).
3. Management
IT is supposed to do more with less. That’s the mandate. Innovate, while reducing operating costs. It’s a constant challenge. It’s why solutions need to do more for less. But when it comes to network security…threats, regulations and complexity continue to increase, while IT security budgets lag – there’s a gap between organizations’ self-defense and the threats they face. To combat this issue, midsize organizations need security solutions that offer a single pane of glass for management, and solutions that simplify policy creation and integrate across multiple applications.
These three challenges are driving UTM adoption in the mid-market. By combining AV, IPS, firewall, application control, DLP and other security features, UTM can consolidate the visibility of threats, save the organization money, and can increase management and reporting efficiency. And, as threats continue to evolve, UTM will evolve with it, adding new security services and giving organizations the ability to easily visualize their security data (instead of simply reviewing log reports).
For more information on this topic, please view the webinar from WatchGuard Technologies, download the infographic, or visit WatchGuard Technologies UTM product page.
Keep your eye out for these five top threats and follow WatchGuard Technologies basic security tips and you’ll surely enjoy a happy holiday season, and hopefully nab a cool treat for you and your family during this shopping season.